In this article, we’ll look at how to manage local administrator passwords on a domain joined computers using the official Microsoft tool – LAPS (Local Administrator Password Solution).
The issue of password managing for the built-in accounts on domain computers is one of the most important security aspects requiring attention of a system administrator. Indeed, you shouldn’t allow using the same local administrator passwords on all domain computers. There are many approaches to the management of local administrator accounts in a domain, from disabling them completely (not too convenient) to managing them using GPO logon scripts, or creating your own password management systems.
Earlier, the Group Policy Preferences (GPP) were often used to change local administrator passwords on a domain joined computers. However, later a serious vulnerability was found in the GPP, which allows any domain user to decrypt a password stored in the text file in the SYSVOL directory on the AD domain controllers. In May, 2014, Microsoft released a security update (MS14-025 – KB 2962486), which completely disabled the feature of setting local user password using GPP.
LAPS Tool: Local Administrator Password Solution
Important. Previously, the LAPS utility was called AdmPwd, but in May 2015, Microsoft released an official AdmPwd version named LAPS, thus transferring it from a third party script to officially supported solution.
The LAPS (Local Administrator Password Solution) tool allows you to centrally control and manage administrator passwords on all domain computers and store the local admin password and its change date directly in the Computer type Active Directory objects.
LAPS features is based on the Group Policy Client Side Extension (CSE) and a small module that is installed on workstations. This tool is used to generate a unique local administrator password (for SID – 500) on each domain computer. An administrator password is automatically changed in a certain period of time (by default, every 30 days). The value of the current local admin password is stored in the confidential attribute of the computer accounts in the Active Directory, and the access permissions to view this attribute value are regulated by the AD security groups.
You can download LAPS and its documentation here: https://www.microsoft.com/en-us/download/details.aspx?id=46899
The LAPS distribution is available in two versions of installation MSI files: for 32-bit (LAPS.x86.msi) and 64-bit (LAPS.x64.msi) systems.
The LAPS architecture consists of 2 parts. The management module is installed on the administrator’s computer, and the client part is installed on servers and PCs on which you need to regularly change the local administrator password. Before deploying LAPS in the production domain, we recommend that you try it in a test environment, since at least you’ll need to extend the AD schema (irreversible).
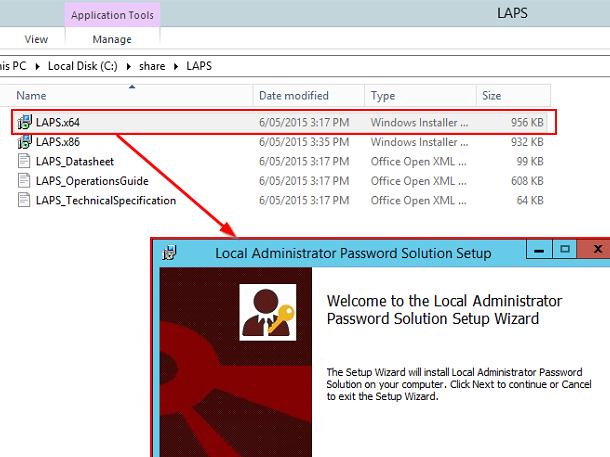
Run the MSI utility file on the administrator’s computer, select all components to be installed (at least .Net Framework 4.0 is required. The package consists of two parts:
- AdmPwd GPO Extension – LAPS executable, which is installed on the client computers, generates and saves the admin password to the AD according to the configured policy;
- LAPS Management Tools:
- Fat client UI – tool to view the administrator password;
- PowerShell module to manage LAPS;
- GPO Editor templates – administrative templates for the GPO editor.
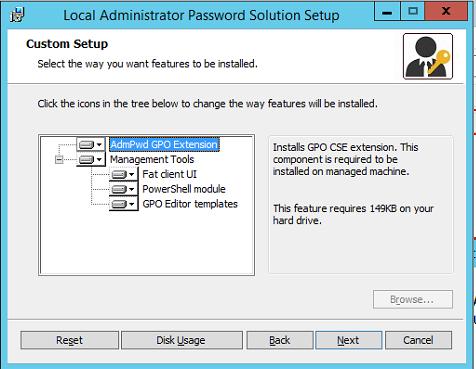
LAPS setup is very easy and shouldn’t cause any problems.
Preparing Active Directory Schema for LAPS Implementation
Prior to deploying LAPS, you have to extend the Active Directory schema to add two new attributes of Computer class.
- ms—MCS—AdmPwd – contains the local administrator password in a plain text;
- ms—MCS—AdmPwdExpirationTime — stores the date when the password expire.
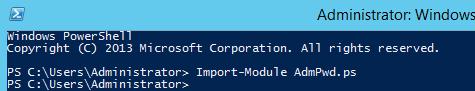
To extend the AD schema, open the PowerShell and import the Admpwd.ps module:
Import-module AdmPwd.ps
Then extend the Active Directory schema (you’ll need Schema Admin privileges):
Update-AdmPwdADSchema
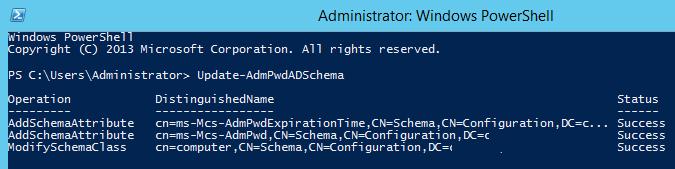
As a result, two new attributes are added to the Computer objects.
Setting Permissions for AD LAPS Attributes
The administrator password is stored in Active Directory attributes as plain text, the access to it is restricted by the confidential AD attributes mechanism (supported since Windows 2003). MS-MCS-AdmPwd attribute can be read by any domain user with the “All Extended Rights” privilege. Users and groups with this permission can read any confidential AD attributes, including the ms-MCS-AdmPwd. Since we don’t want anyone other than domain admin (and/or HelpDesk Support team) to view computer passwords, we have to limit the list of groups with read permissions on these attributes.
Using the Find-AdmPwdExtendedRights cmdlet, you can get the list of accounts and groups having these permissions on the OU with the name Desktops:
Find-AdmPwdExtendedRights -Identity Desktops | Format-Table ExtendedRightHolders
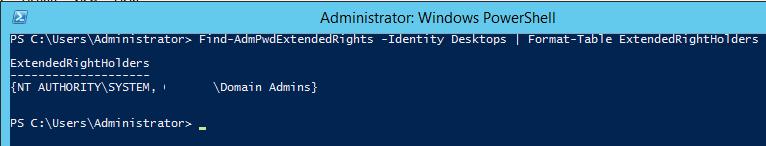
As you can see, only the Domain Admins group has the read permissions on the confidential attributes.
If you need to deny access to read these attribute values for certain groups or users, do the following:
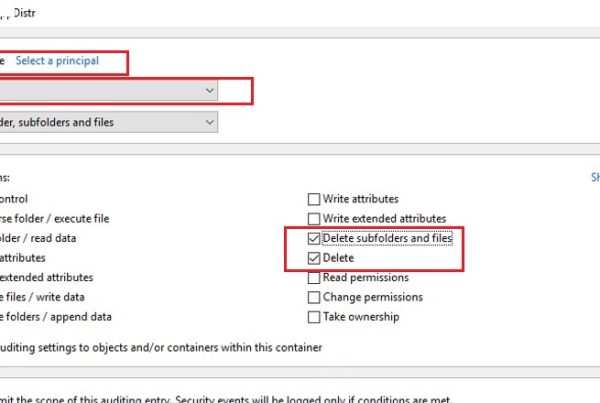
- Open the ADSIEdit tool and connect to Default naming context;
- Expand the domain tree, find the necessary OU (in our example, it is Desktops), right-click it and select Properties;
- Then go to the Security tab, and click the Advanced -> Add button. In the Select Principal section, specify the name of the group/user, you want to restrict the permissions (e.g., domainSupport Team);
- Uncheck the “All extended rights” and save the changes.
Do the same for all groups, for which you want to restrict the local admin password viewing. You will have to restrict read permissions on all OUs, computer passwords in which will be managed by LAPS.
Then you need to grant permissions for the computer accounts to modify their own attributes (SELF), because the values of ms-MCS-AdmPwd and ms-MCS-AdmPwdExpirationTime are changed under the computer account itself. Use another cmdlet Set-AdmPwdComputerSelfPermission.
To grant permission for the computers in the Desktops OU to update the extended attributes, run this command:
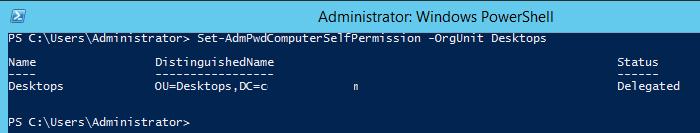
Set-AdmPwdComputerSelfPermission -OrgUnit Desktops
New LAPS computer attributes by default are not replicated to the RODC domain controllers.
Granting Permissions to View LAPS Password
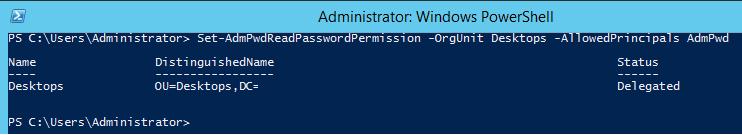
The next step is to grant users and groups the permissions to read local administrator passwords, stored in Active Directory. For example, you want to grant the members of AdmPwd group read password permissions:
Set-AdmPwdReadPasswordPermission -OrgUnit Desktops -AllowedPrincipals AdmPwd
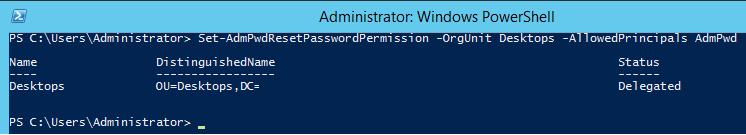
In addition, you can allow a certain group of users to reset computer passwords (in this example, we give it to the same group — AdmPwd):
Set-AdmPwdResetPasswordPermission -OrgUnit Desktops -AllowedPrincipals AdmPwd
How to Configure LAPS Group Policy Settings?
Then you have to create a new GPO object and link it to the OU containing the computers, on which you want to manage local administrator passwords.For easy GPO management, you can copy the LAPS administrative template files. (%WINDIR%PolicyDefinitionsAdmPwd.admx and %WINDIR%PolicyDefinitionsen-USAdmPwd.adml) to the Group Policy Central Store — \domain.comSysvolPoliciesPolicyDefinition.
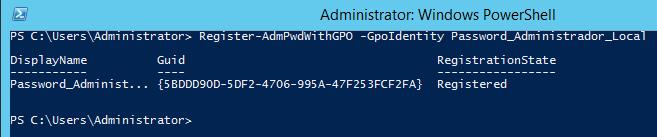
Create a policy with the name Password_Administrador_Local using the following command:
Register-AdmPwdWithGPO -GpoIdentity: Password_Administrador_Local
Open this policy in the Domain Policy Management Console (gpmc.msc) and go to the following GPO section: Computer Configuration -> Administrative Templates -> LAPS.
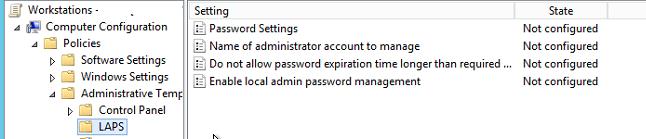
As we can see, there are 4 customizable settings. Configure them as shown below:
- Enable local admin password management: Enabled (enable the LAPS password management policy);
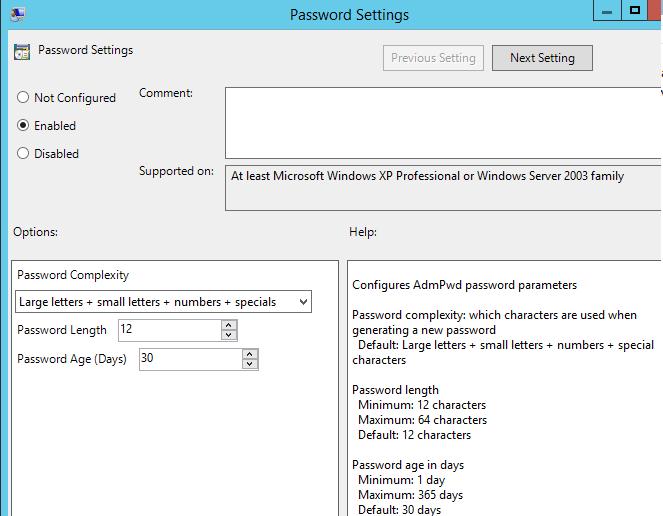
- Password Settings: Enabled – the policy sets the password complexity, length and age;
- Complexity: Large letters, small letters, numbers, specials
- Length: 12 characters
- Age: 30 day
- Name of administrator account to manage: Not Configured (here you can specify the name of the administrator account to change password. By default, the password of the built-in administrator accounts with SID-500 is changed.);
- Do not allow password expiration time longer than required by policy: Enabled
Assign the Password_Administrador_Local policy to the Desktops OU.
Installing LAPS Agent on a Domain Computers via GPO
After you configured the GPO, it’s time to install LAPS client part on the domain computers. The LAPS client can be distributed in different ways: manually, via the SCCM task, a logon script, etc. In our example, we’ll install the MSI file using the feature of MSI package installation in the group policies (GPSI).
- Create a shared network folder on a file server (or use the SYSVOL folder on the domain controller) and copy the LAPS distribution msi files into it;
- Create a new GPO and in the Computer Configuration ->Policies ->Software Settings -> Software Installation section create a task to install the LAPS MSI package.
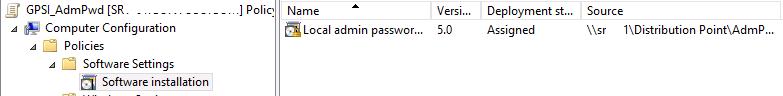
Please note that there are x86 and x64 versions of LAPS. To install the package on the appropriate Windows version, you can make 2 separate LAPS policies with WMI GPO filters for x86 and x64 editions of Windows.
You only have to assign a policy to the necessary OU, and after the restart, the LAPS client should be installed on all computers in the target OU.
Make sure that the record Local admin password management solution appeared in Programs and Features in the Control Panel.
When the LAPS utility changes the password of the local administrator, it is registered the event in the Application log (Event ID:12, Source: AdmPwd).
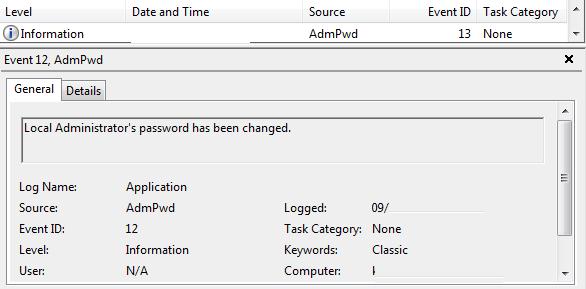
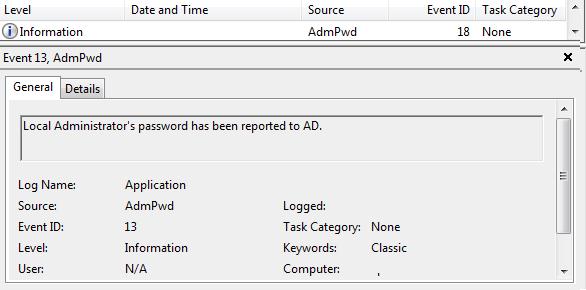
The event of saving the password to the AD is also registered (Event ID:13, Source: AdmPwd).
This is how new attributes look in the Attribute Editor tab in the AD computer properties.
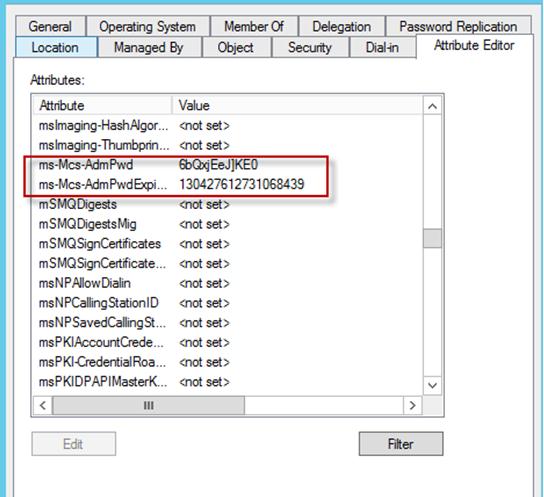
Tip. The time of password expiration is stored in the “Win32 FILETIME” format .
Using LAPS to View Administrator Password
LAPS graphic interface (GUI) to view LAPS passwords must to be installed on the administrator computers.
If you start the tool and specify the computer name, you can view the local administrator password and its expiration date.
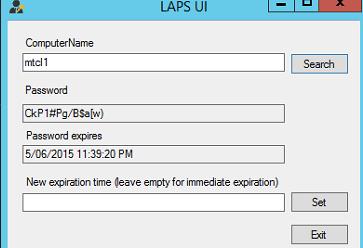
Password expiration date can be set manually, or leave this field empty, and by clicking Set specify that the password has already expired.
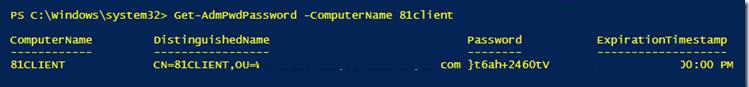
Also, you can get the computer password using PowerShell:
Get-AdmPwdPassword -ComputerName <computername>
If you think that local administrators’ passwords on all computers in some OU are compromised, you can generate new unique local admin passwords for all computers in the OU with a single PowerShell command. To do this, use the the Get-ADComputer cmdlet:
Get-ADComputer -Filter * -SearchBase “OU=Desktops,OU=NY,OU=USA,DC=contoso,DC=com” | Reset-AdmPwdPassword -ComputerName {$_.Name}
Similarly, you can display a list of current passwords for all computers in the OU:
Get-ADComputer -Filter * -SearchBase “OU=Desktops,OU=NY,OU=USA,DC=contoso,DC=com” | Get-AdmPwdPassword -ComputerName {$_.Name}
LAPS can be recommended as a convenient solution for organizing a secure password management for a domain computers with the possibility of granular access control to passwords for computers in a different OUs. The passwords are stored in the Active Directory computer attributes a in plain text, but the built-in AD tools allow you to securely restrict access to them.